What Is Secure SDLC and Why Does It Matter?
Building Safe Software from the Ground Up: Understanding the Importance of Secure SDLC
The Software Development Life Cycle (SDLC) is a roadmap for creating software. It covers every step, from planning features to post-release updates.
The Secure SDLC (SSDLC) follows the same path but prioritizes security at every stage.
If you want to transition to DevSecOps, you’ll need to implement an SSDLC.
In this guide, we’ll explore what an SSDLC involves, why it’s needed, and its benefits.
What Is the Secure Software Development Life Cycle?
The Secure SDLC is a framework that integrates security into each phase of the development process. While the traditional SDLC focuses on functionality, performance, and user experience, SSDLC makes security an equal priority.
The goal is to make software that is functional but also safeguarded against potential threats. It’s about building a product that does its job and keeps data and users safe.
The Need for SSDLC
Making a successful software product isn’t easy. It takes a lot of effort, dedication, and teamwork. You don’t want that hard work to go to waste due to a security oversight that compromises user data.
Cyber threats are evolving and becoming more sophisticated and aggressive. From ransomware attacks to data breaches, the repercussions are serious - and expensive.
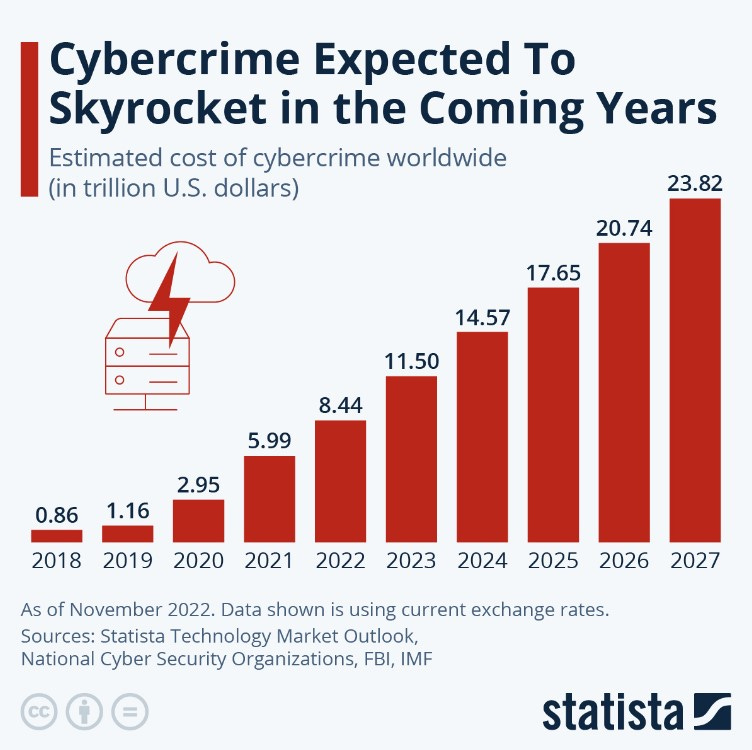
The cost of cybercrime is set to hit $23.82 trillion by 2027:
That’s why its crucial software is built with security in mind from the beginning. That’s why we need SSDLC.
Key Stages of the SSDLC
You’re probably familiar with the standard SDLC. It provides a framework for building software.
The SSDLC approach is about minimizing vulnerabilities. Security is integral to the development process, not just an afterthought.
Let’s break down how that looks in practice for each stage of the SDLC:
1. Planning
Before starting a project, you establish the goals, scope, and resources required. You’ll research users, speak to stakeholders, and analyze competitors. Doing this gives you a clear picture of what’s needed and how best to design and develop your product.
SSDLC Addition:
Risk Assessment
When determining what the software will do, you also analyze potential security threats and vulnerabilities the software might face when operational.
Compliance Requirements
Relevant legal and regulatory standards are integrated into the project based on the software's purpose. For example, financial software must align with banking regulations.
Stakeholder Education
The SSDLC goes beyond consulting stakeholders about functionality. You make a plan to educate stakeholders about security through workshops and training.
2. Design
This is where you decide how the software will work and what it will look like. The architectural layout is crafted considering aspects like performance and scalability. A technical specification is developed, itemizing software functionalities, including inputs, processes, and outputs.
SSDLC Addition
Threat Modeling
Potential software vulnerabilities are identified and assessed. The insights are fed back into the process so the design can be modified to address security risks before they manifest.
Secure Design Principles
Adopt design principles that emphasize security. This could mean ensuring minimal attack surfaces, employing the principle of least privilege, and more.
3. Build
You start writing the actual code for the software based on the design. The design specifications are translated into functional software and an executable application.
SSDLC Addition:
Secure Coding
Developers adhere to secure coding practices like input validation and proper error handling. The goal is to mitigate common vulnerabilities like SQL injection. There are a bunch of DevSecOps tools you can use to help secure your environment.
Limited Access
Only give access rights to those who really need them. Limiting who can see or change certain parts of the software can reduce risks. This guideline should be implemented throughout the entire SDLC.
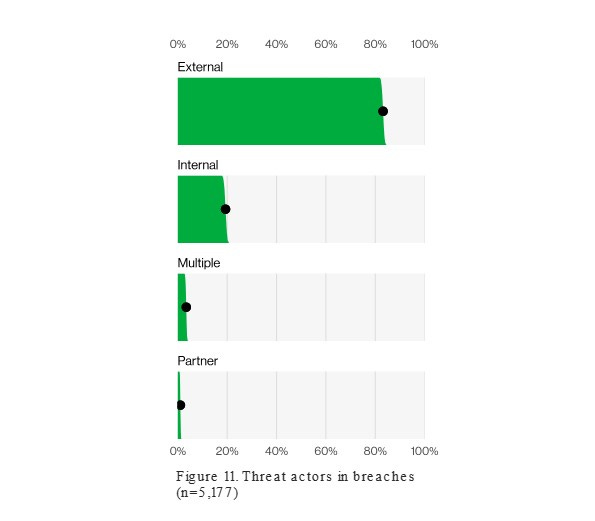
A recent Verizon study found that internal actors are responsible for 19% of data breaches:
Static Application Security Testing (SAST)
SAST is a set of tools designed to review an application’s code without execution to identify security vulnerabilities. Integrated SAST into the build workflow can offer real-time feedback. This can help the development team resolve vulnerabilities before testing and deployment.
4. Release (Testing & Deployment)
Once the software is built, it’s tested to find and fix any errors or bugs. This includes functional testing to assess responsiveness and stability. It can also involve usability testing to improve the user experience.
After testing, the software is deployed. This might mean releasing it to the public or just to a specific group of users.
SSDLC Addition:
Security Testing
The software undergoes automated and manual evaluations to detect potential security flaws, including:
DAST - Automated testing that checks for vulnerabilities during the application’s active state.
Penetration Testing - Ethical hacking techniques to simulate real-world attacks and uncover security gaps.
System Hardening
The software and its environment are strengthened to reduce vulnerabilities. This can include disabling superfluous services, applying security patches, and setting up access controls.
Security patches are the big thing here. In Europe, 34% of IT professionals say their organization has experienced a breach due to an unpatched vulnerability:
5. Maintenance
After the software is released, work continues, fixing new problems and adding new features. As users interact with the software, bugs may come to light. When they do, prompt measures are taken to resolve them.
New features are added based on user feedback and technical evaluations.
SSDLC Addition:
Security Monitoring
The software is monitored to detect unauthorized access attempts, suspicious behavioral patterns, or potential data breaches.
Transparent Communication
One of the hallmarks of the SSDLC approach is clear, transparent communication. Whether it’s software updates, potential threats, or security incidents.
You can use a tool like Instatus to manage user communication. It’s a simple and effective way to provide real-time updates to users about software status and security incidents.
Post-Update Security Evaluations
Software updates can open new vulnerabilities. Each software change undergoes a security impact assessment, which can include secure data handling for new features or ensuring third-party integrations meet security standards.
6. Replacement and Retirement
Eventually, the software will be decommissioned due to obsolescence or replaced by a more advanced solution. Before retiring software, it’s crucial to ensure all necessary data is backed up or migrated. This stage can also involve helping stakeholders manage the transition to the new solution.
SSDLC Addition:
Data Security
Data management is the key thing here. Sensitive data can be permanently deleted to safeguard against future unauthorized access. Any data that needs to be retained should be securely archived with encryption and strict access controls.
Post-Mortem Analysis
The final step is to review any security incidents and challenges during the SDLC. This review can reveal lessons for future projects.
Benefits of Adopting SSDLC
Many of the tasks involved with the SSDLC already take place during a standard software development project. The big difference is that these security considerations are prioritized throughout each stage.
This can bring several benefits:
Proactive Defense
You can find and fix weaknesses before anyone tries to take advantage of them. Instead of waiting to see if something goes wrong, steps are taken in advance to prevent those problems from happening in the first place.
Addressing vulnerabilities early on makes the software more robust. It’s less likely to be compromised by potential threats.
Cost-Efficiency
The cost is usually lower when security issues are identified and fixed early. Fixing a minor issue during the development phase often requires less time and fewer resources than solving a big problem post-deployment.
If you discover a vulnerability after the software is already in use, you must inform affected users, investigate the issue, and implement emergency fixes. If data is compromised, you may even have to cover legal fees and fines.
That’s why fixing a bug during the post-release stage is up to 30 times higher than during the requirements stage.
Trust Building
Security is a significant concern for software users. If they feel an application is unsafe or their personal information might be at risk, they won’t use it.
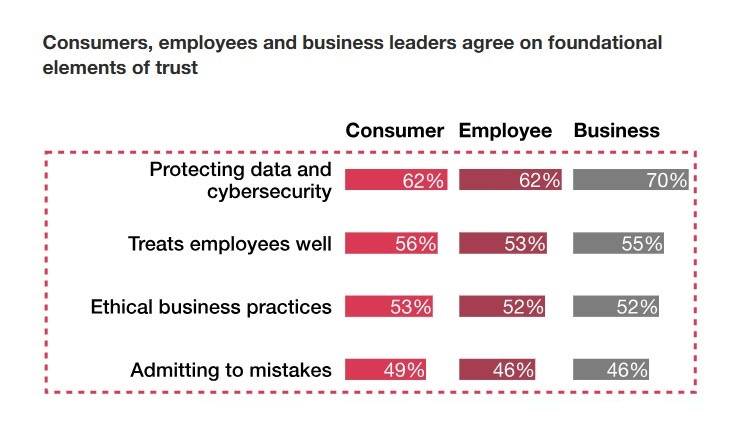
According to a recent study by PwC, 62% of consumers view data protection and cybersecurity as a foundational element of trust when dealing with a company.
The SSDLC helps to protect that trust. It’s about making safer software and minimizing the risk of security issues.
Conclusion
Security isn’t an added feature or a box you need to tick before deployment. It’s a necessity.
The SSDLC provides a structured approach to integrate security throughout the development process. By prioritizing security, you can build products that users trust. You can also reduce risks and potential costs related to breaches or vulnerabilities.
A commitment to security in software development is an investment in the overall success of any software product.